In Part 1 of our Q&A with Raja Paranjothi, Senior Manager of Business &Technology Risk Services with Mayer Hoffman McCann P.C. (MHM), we looked at how large data breaches amongconsumer retail giants such as Target, Neiman Marcus and Michaels
– are intensifying both corporate and regulatory attention to physical, environmental and information security controls among business value chains. While our discussion focused on contingent workforce partners, the discussion is applicable to each link in the value chain based on services provided.
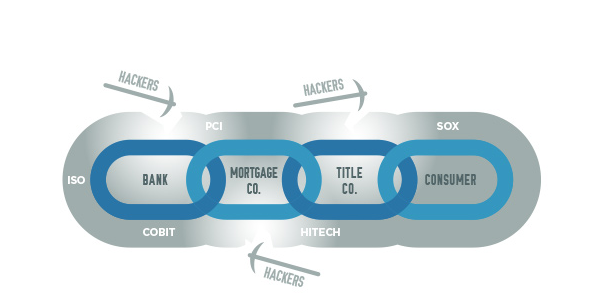
Here in Part 2, Paranjothi fills in more details to help talent strategists understand how certifications or compliance to control standards such as a SSAE 16 or SOC report can fit into their thinking and due diligence for meeting contingent workforce requirements while also identifying, managing and mitigating cascading risk throughout their business-value chains.
Q: As a services provider ourselves we have seen dramatic increases in both the number and rigor of control-related questions and requirements in Requests for Proposals (RFPs) from potential clients, especially from financial services companies. So, is a SOC report typically comprehensive enough to satisfy most customers’ requirements?
A SOC report should cover the bases of what most clients would be looking for. But it is very important to understand that each SOC report is unique and not all are created equal. The first thing I would look at is who created the report. Is it a reputable accounting firm with sufficient expertise and investment in this area? There are some smaller CPA firms who will perform SOC reporting for small fees, but the quality of the reporting may not be as comprehensive.
Aside from who creates the report, I would look carefully at which controls have actually been tested. Very often, the scope of the SOC report will not be a perfect fit for every client. What is more, SSAE 16 is just one of many control standards out there. There is also NIST, ISO, COBIT, PCI, HIPAA, NERC and others. Every one has an opinion on what is the best standard to follow and it is quite likely that most clients will continue to find areas where they wish to supplement with their own requirements based on their risk appetite. We often see service providers trying to map to various standards so they will be covered for any standard a potential client may want to see. But, as long as we continue to have multiple competing standards, I believe we will continue to see companies customizing the risk-related questions they ask of their suppliers and service providers.
Q: From a control standards adoption standpoint, are you seeing certain industries higher on the maturity curve than others?
Financial services, government, healthcare and IT companies are probably the most mature with respect to mandating adherence to controls standards among their suppliers and service providers. Government entities will often use the NIST standard. For healthcare, of course it is HIPAA. IT companies will often look for ISO, NIST or COBIT. Another industry we are starting to see a lot of play in is real estate and titles. The mortgage banks are driving that, so it is really part of the domino effect from financial services that we were discussing earlier. Some of the title companies are quite small, so the annual costs of undertaking SOC or similar reporting can be a big financial burden. Unfortunately, it’s a necessary cost of operating in industries that handle sensitive data.
Q: So, if one is considering a delivery center that already serves one or several of these mature industry segments, is it a safe bet that the delivery center would be ahead of the curve on compliance to various logical and physical control standards?
Yes, I think that’s a fair assessment. Our new clients always want to know if we are familiar with their industry because it signifies that we already speak their language and are familiar with their particular concerns. I believe the same thing would apply here with certified delivery center providers.
Q: Can you describe the SOC audit process for us?
The first thing we always do is a readiness assessment. We go on site for about three days, walk through the service providers’ processes and observe how they conduct their business from a day-to-day perspective. We make sure that we really understand the business first. Based on our initial interviews, we give the service provider (our client) a gap analysis, outlining where they are okay and what they need to fix. We also give them a draft report; essentially, we design the controls we think they need and give them a draft of what we believe their final report will look like once those controls are implemented and tested.
Each client’s report is customized, depending on the services they provide to their customers. When we design a SOC report, we start by asking what the service provider’s clients would care most about. A big dividing line is whether or not the service provider hosts data for its clients because that opens up so many more logical and physical security questions. For an outsourcing delivery center, the client’s concerns will typically be around logical and physical security, on- and off-boarding of consultants and things of that nature. While there are core components that are fairly standard across SOC reports, the design for each company is very much a function of the services provided and what the service provider’s customers care most about. This also could evolve from year to year based on the evolution of services provided, new regulatory guidance influencing an industry or the addition of new clients in a specific location. The latter is relevant because SOC reports can be site specific.
Q: For someone reviewing a SOC report, what two or three things would you advise them to focus on in terms of evaluating the validity and strength of the report?
I would start by reading the CPA firm’s opinion, which comes right at the beginning. Second, I would look at the User Control Considerations (UCCs). These are the controls that the client needs to worry about because the service provider is essentially stating it does not assume responsibility for those. In a delivery center setting, this might include VPN access to client servers, for example, which is controlled by the client. The UCC section is essentially saying, ‘Here are the things we can not control, so they are your responsibility, not ours.’ After that, I would look through the major sections of the report. This will help one to quickly understand if all the important high-level areas are covered.
Q: If you were evaluating competitive bids from a series of outsourcing services providers, how would SOC reporting fit into your weighing of the candidates?
Having a SOC report is certainly a big differentiator from not having one. It demonstrates an understanding of the importance of managing and maintaining a secure work environment to minimize client risk as well as financial wherewithal. And the investment goes beyond fees associated with generating the SOC report. Very often the service provider needs to make changes to come into compliance and those changes carry material costs.
With that said, there are many differences among SOC reports, so you need some education and experience to be able to spot the nuances. As a person who builds SOC reports professionally, I can thumb through one and identify gaps very quickly. If it is not something you do every day, it can be more challenging to find the small things that might tell you a report is scoped improperly or has been created by a firm that does not have the necessary expertise.
If I did not easily recognize the name of the accounting firm that created a SOC report, I would investigate them online and look for evidence of expertise in implementing to SSAE 16 standards. I might also recruit internal experts from various functions – IT, security, finance, procurement and so forth – to assist in the review of a SOC report as each will look for different things and may be able to spot what is missing from the report as well as aid the client in identifying areas to take a closer look.
Q: Is there a global counterpart for the SSAE 16 standard that one might look for in comparing a global offshore to domestic outsourcing services providers?
ISO is very big internationally across Europe and Asia. You will often see that standard in use, but it is more engineering driven. The latest update to SSAE 16 is comparable to the international standard ISAE 3402.
Regardless of there being comparable global standards, where Cloud data is concerned, we would always advise our clients to stay within U.S. borders. Every country has different rules and laws, so if you want to be totally safe and protected, we advise them to keep data here in here U.S. Of course, that won’t always be feasible for international corporations, but if they are using Cloud providers for anything, we see it as a red flag if they cannot tell us precisely where their data is located. Amazon, for example, has the biggest data center operation in the world and their data centers are spread out around the globe. They are pretty good about disclosing which region a company’s data is located in physically.
Q: What are some specific examples of things you typically will ask delivery centers to do or change in order to come into compliance with SSAE 16?
Documentation – in terms of policies and procedures - is often lacking, so we will want to see those things updated with an established update routine, which is clearly documented. There may also be aspects of logical security they need to lock down. Periodic user reviews by management is another big one. Whether monthly, quarterly or semiannually, we want to see consistent periodic reviews of who has logical access to applications, networks as well as physical access to buildings. Change control is another area we nearly always find ourselves putting into place. So, for example, if they are going to perform maintenance or updates to an application, system or network, we want to see certain procedures being executed including appropriate management approvals, testing, backups, documentation and things of that nature.
Q: How often should one expect to see an updated SOC report from a service provider and should one expect the content to change substantially?
SOC reports should be updated every year. They are living documents that evolve and change each year as the service provider expands its scope or changes the services it provides to clients. An outsourcing delivery center, for example, might add a new location. Because it is a physical place, we would need to scope in the security for the new physical location. While each location would need to be scoped into the SOC report, we would also be looking for consistency from one location to the next. That benefits both the delivery center and its clients as compliance standards and consistency signify both maturity and operational efficiency on the part of the service provider. As a third-party auditor, we can often be more successful at driving to standards and consistent processes than internal personnel might be because it’s okay for us to be the bad guys.
Q: We have been focusing on controls and compliance relative to outsourcing delivery centers, but are there similar implications in this discussion for more traditional consulting or contingent staffing arrangements as well?
From traditional consulting or staffing perspectives, the most important controls to me are related to candidate selection, vetting (background check and so forth), on- and off-boarding processes, asset management and logical & physical security.
Important variables to always consider are where a consultant or flex staffer (staff supplementation) will work, who owns and controls the devices they use and how they access digital networks. If they work from home or an offsite office, you may have greater exposure to physical risks compared to either onsite or a delivery center that has been certified to certain control standards and provides management oversight. For example, the home or offsite office may be less secure to intruders. Or the consultant or worker may have a habit of tossing printed documents containing sensitive information into a recycling bin or trashcan rather than shredding as one example. You also have less or no direct oversight than you would if they worked onsite or in a delivery center that has been certified to various physical and environmental control standards. Much of the same can be said, however, for all work-at-home or otherwise remote work arrangements even with permanent employees.
Device ownership is important because the hiring company can always prevent its own devices from transferring information to external storage devices, but it won’t have that control over devices owned by consultants or contingent workers. Logical access is likewise important. If the consultant or contingent worker hits a hiring company’s network by VPN using a device the hiring company owns (which is fairly standard practice), they would have at least the same level of control and risk mitigation as with their own employees performing work from home, business hotel rooms or elsewhere.
At the end of the day, you have to assume that technology will continue to advance. More and more sensitive data is going to become digitized, aggregated, distributed, moved around electronically, stored, backed up and hosted remotely. All of those circumstances create vulnerabilities and risk exposures throughout business value chains that consumers, business leaders and government regulators are going to be paying very close attention to in coming years. There will continue to be multiple standards for control and compliance procedures that attempt to mitigate risks to the greatest extent feasible. Being aware of and understanding the various standards will need to be a core competency for talent strategists as they continue to adjust staff-to-flex ratios and include greater numbers of outsourced, remote and otherwise disaggregated and distributed work arrangements.















