By the numbers, the FBI Cyber Division recently reported a staggering increase in the number of cyber incidents reported to as many as 4,000 per day, which is approximately a 400% increase pre-COVID-19. According to a recent report by Kaspersky, there have been 726 million confirmed cyberattacks since the start of the year, putting us on track for approximately 1.5 billion cyberattacks in 2020.

The global pandemic, like a flip of a switch, changed how businesses operate with little to no warning. One day we are in the office and the next we are working from our kitchen table. As everyone moved online, there were a lot of companies that were not prepared, creating the perfect storm for the dark web and cyberattacks. Still, the kinds of cyberattacks remain the same, whether it is through phishing, downloading malware or through social engineering and gaining access to credentials. According to Mimecast’s State of Email Security 2020 Report 72% of respondents report an increase in phishing incidents due to the pandemic as well as a 30% increase of impersonation fraud attempts from January to April 2020.
Cybercriminals are exploiting the situation, creating a playground to launch sophisticated cyberattacks and no industry is immune. There have been several high-profile data breaches thus far in 2020 to include Microsoft, Twitter, Marriott, Fifth Third Bank, Cognizant, and Zoom to name a few. Hackers have stolen customer information to include social security number or financial data as well as account credentials which broadens access to internal systems. These breaches generate negative publicity and impact brand and reputation.
“It is important to understand and keep in mind that when it comes to cyberattacks there are sophisticated nation state attack tools that were leaked a few years ago to the dark net, which are available for sale. It is as simple as that! “Civilian” hackers have access to the most advanced cyber war tools. Anyone anywhere is a target,” According to Ran Shahor, CEO & Co-Founder, HolistiCyber.
When the world went remote, it created more vulnerabilities for every company because there are more endpoints with access to the corporate network. An endpoint could be a phone, desktop, laptop, or really any device that connects the employee to the corporate network. Hackers know there is an increased likelihood of weakness targeting exposed endpoints, servers (DNS, VPN, RDP, etc.) and the cloud. Some companies could be at risk due to poor configuration of the cloud architecture, creating another stairway into the organization. A recent study published by Acronis highlights the variety of cyberattacks to include Distributed Denial of Service (DDoS) where a website or web application or server becomes overwhelmed with fake traffic and cannot support legitimate users.
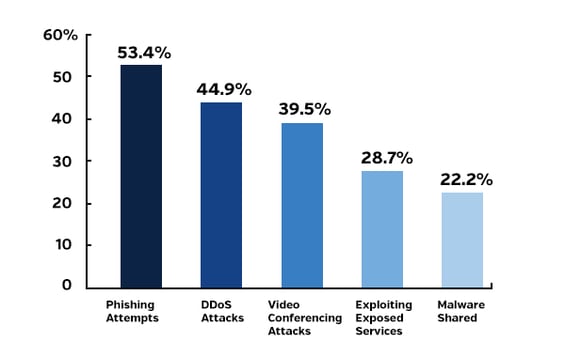
You know the problem; now how will you prepare your company to respond? The basics include installing antivirus, firewalls and software to detect phishing and malware as well as to conduct employee cybersecurity training.
3 Tips to take cyber readiness and resiliency to the next level:
 Conduct Threat Modeling and a Tabletop Simulation
Conduct Threat Modeling and a Tabletop Simulation
The more that you understand about your business operations, the applications that you are dependent on and where valuable data resides, then the more prepared you will be if an attack occurs. Consider completing threat modeling and simulation exercises to help practice what each person would do to include engagement with the media if you fall victim to an attack.
According to a recent article in Forbes, The Important Difference Between Cybersecurity And Cyber Resilience (And Why You Need Both), once you gain an understanding of how core functions could be affected, “cyber resilience involves putting in place measures to mitigate the damage…. For example, develop offline emergency processes to keep essential functions running until the breach is fixed.” In addition to a cyber resilience plan, a cyber response plan and team should also be structured to efficiently mobilize in the event of a breach.
Identity and Access Management
COVID-19 has shined a light on the need for modern identity and access management controls. Typically, an organization has provisioned to support a percentage of their organization in a remote capacity, not 100% of the workforce. Therefore, the ability to rapidly scale as well as mange secure access to legacy applications can create a hurdle. Multi-factor authentication with session management coupled with modern access management tools such as SAML or OAuth 2.0 offer options to mitigate against account takeover or phishing attacks. But with anything, there are trade-offs and a comprehensive review of your architecture and requirements should be completed before moving forward with tool selection. According to Gartner, “one of the largest mistakes organizations make when enabling any remote access technology is not defining requirements before purchasing and deploying products. This often results in poor performance, user dissatisfaction, and lesser security as users try to circumvent deployed security solutions in order to have better usability.”
Block and Tackling – Maintain a Patching Cadence
Keeping up with the patching schedule to manage and mitigate threats can be challenging with competing priorities and an increased project workload. Genesis10’s patching factory service can earmark a dedicated team of proven professionals to effectively manage resources and adjust both the patching priorities and schedules dynamically.
 Read this case study to learn how Genesis10 helped a multinational financial services client who was facing regulatory findings implement a server patching cadence and move from red to green status.
Read this case study to learn how Genesis10 helped a multinational financial services client who was facing regulatory findings implement a server patching cadence and move from red to green status.
There is no silver bullet outside of good old-fashioned planning, anticipating, and having solid partners to back you up.














